As cyber threats evolve, organizations should prioritize safe distant entry options. Historically, Digital Non-public Networks (VPNs) are the go-to for safe connectivity. Nonetheless, Zero Belief Community Entry (ZTNA) is rising as a better various, providing enhanced safety and adaptability.
This text compares ZTNA and VPNs, analyzing their strengths, weaknesses, and suitability for contemporary cybersecurity challenges.
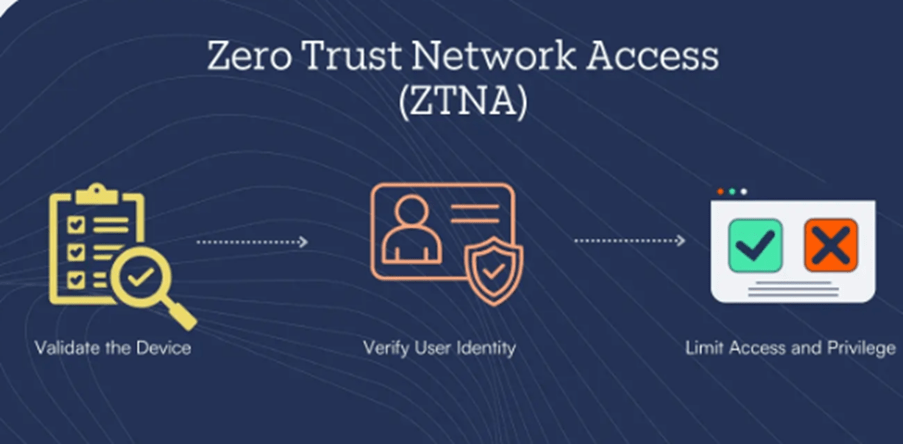
What’s Zero Belief Community Entry (ZTNA)?
Due to Aztech
Zero Belief Community Entry (ZTNA) is a cybersecurity framework that implements strict entry controls based mostly on id, machine safety posture, and contextual elements. Not like VPNs, ZTNA follows the Zero Belief precept—”by no means belief, at all times confirm.”
Three Key Rules of a Zero-Belief Safety Mannequin
- Ongoing Verification: No person or machine could be trusted, and verification needs to be an ongoing course of. Verification entails authenticating customers and units by varied strategies, akin to multi-factor authentication or biometric information, and verifying the person and machine standing even after the preliminary entry is granted.
- Minimal entry: By segmenting the community to create minor zones of management, organizations can management entry to purposes, information, and assets and grant least-privilege entry based mostly on want or position. This strategy lessens the assault floor and limits the potential injury from a breach.
- Assume breach: Organizations ought to plot as if attackers are already inside and outdoors the community. This mindset requires organizations to forgo the standard idea of a “trusted zone,” akin to “within the workplace,” and undertake a extra versatile and adaptable strategy to safety.
Additionally learn: High 15 Important Open Supply Cyber Safety Instruments for 2025
How ZTNA Works
ZTNA features on a software-defined perimeter (SDP) that verifies person id, machine safety posture, and contextual information earlier than granting entry. As a substitute of permitting broad community entry, ZTNA permits customers to attach solely to approved purposes and assets by a cloud-based dealer or gateway. This structure enhances safety by segmenting entry and lowering the assault floor.
ZTNA works with an id supplier to authenticate customers and units and applies multi-factor authentication (MFA) to further safe distant connections.
It doesn’t depend on the general public web connection but in addition integrates with the cloud setting to make sure safe, seamless distant entry options for distant and hybrid employees.
Use Circumstances of ZTNA
- Distant Workforce Safety: It supplies safe entry to company purposes with out exposing the community.
- Cloud and Hybrid Environments: Smooths safe entry throughout multi-cloud and hybrid infrastructure.
- Third-Celebration and Vendor Entry: Ensures managed, least-privileged entry for exterior customers.
- Compliance and Regulatory Necessities: Helps organizations meet strict safety requirements and compliance mandates.
What’s a Digital Non-public Community (VPN)?
Due to Aztech
A Digital Non-public Community (VPN) is a safe connection that encrypts information and routes it by a non-public server, masking the person’s IP handle. VPNs are broadly used for distant entry, enabling workers to hook up with company networks securely.
VPNs usually depend on protocols akin to safe socket tunneling protocol (SSTP), Level-to-Level Tunnelling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Web Key Change Model 2 (IKEv2) to construct a safe connection over the general public Web.
This implies the person’s site visitors is routed by the VPN shopper, which encrypts their information and provides them entry to the required company assets, although typically with much less granular management than ZTNA.
Additionally Learn: Unlock Limitless Streaming with 10 Greatest VPNs
Advantages of VPNs:
- Safe Knowledge Transmission: Encrypts information to stop interception.
- Distant Entry: Permits customers to hook up with company networks from any location.
- Anonymity: Hides IP addresses to reinforce privateness.
- Compatibility: VPNs work throughout a number of working methods and units, providing safe distant entry to varied endpoints.
Limitations of VPNs:
- Broad Community Entry: As soon as authenticated, customers have entry to the complete community, rising the chance of lateral motion by attackers.
- Efficiency Points: VPNs can decelerate connections as a consequence of encryption overhead and server congestion.
- Scalability Challenges: Managing VPNs for a big workforce could be advanced and dear.
- Legacy expertise: Some VPN options are outdated and should not combine properly with fashionable cloud or hybrid infrastructures.
ZTNA vs VPN: A Detailed Comparability
| Characteristic | VPN | ZTNA |
| Safety Mannequin | Perimeter-based safety | Zero Belief precept |
| Entry Management | Broad community entry | Granular, least-privilege entry |
| Efficiency | Could be gradual as a consequence of encryption overhead | Optimized cloud-native connectivity |
| Scalability | Troublesome to scale for big enterprises | Simply scalable throughout cloud and hybrid environments |
| Assault Floor | Increased threat as a consequence of full community entry | Decreased assault floor with application-specific entry |
| Implementation | Simpler however could require extra safety measures | Extra advanced however provides superior safety |
Due to Fortinet
Which One Ought to You Select?
Selecting between ZTNA and VPN is dependent upon your group’s safety wants and infrastructure:
Use VPN if
- You want a fast and cost-effective answer for distant entry with minimal safety restrictions.
- There are eventualities the place broad community entry is required or working inside legacy methods requiring network-level entry.
- VPNs are a very good match for smaller companies with a couple of distant workers, defending unsecured Wi-Fi.
Use ZTNA if
- You prioritize safety, want granular entry management, and desire a scalable answer for cloud and hybrid environments.
- There are bigger organizations with distant or hybrid groups, as they implement stricter entry controls for delicate information and purposes.
Additionally Learn: Cybersecurity: Important Ideas and Greatest Practices for Defending Private and Enterprise Knowledge within the Digital Age
ZTNA vs VPN: Components to Think about When Selecting Them
Listed below are the elements to contemplate whereas selecting ZTNA and VPN options:
Safety wants
If minimizing the assault floor and controlling entry to particular purposes are high priorities, ZTNA provides higher safety by granular management.
Scalability
ZTNA options are normally extra scalable, particularly within the cloud environments. VPNs could turn out to be much less environment friendly as extra distant employees join.
Integration with fashionable IT methods
In case your group makes use of a fusion of on-premise and cloud assets, ZTNA could be the higher possibility, because it flawlessly integrates with cloud platforms.
Consumer expertise
VPNs can generally trigger efficiency points, whereas ZTNA provides a extra seamless person expertise with fewer slowdowns.
Value
VPNs are normally cheaper upfront, however the greater safety dangers and administration complexity can improve prices in the long term.
Summing Up:
Whereas VPNs have been a trusted answer for years, ZTNA provides a extra superior and safe strategy to distant entry. As cyber threats turn out to be extra refined, companies ought to think about transitioning to ZTNA to reinforce safety, cut back assault surfaces, and enhance efficiency. The way forward for cybersecurity lies in Zero Belief fashions, making ZTNA the popular alternative for contemporary enterprises.
FAQs
What’s the distinction between a standard VPN and SASE?
The important thing distinction between a standard VPN and SASE is that VPNs safe solely the connection, whereas SASE combines community and safety companies within the cloud. SASE provides extra complete safety for distant and cloud environments, whereas VPNs are extra conventional and restricted to entry networks.
What’s the distinction between an At all times-On VPN and Zero Belief?
An always-on VPN supplies steady, broader entry to networks, whereas ZTNA operates on a zero-trust precept, granting entry to explicit purposes after verifying the person’s id and machine safety. This implies ZTNA provides safer and restricted entry to networks than VPNs.
Is ZTNA more durable to implement than VPN?
Whereas ZTNA could be extra advanced to implement as a consequence of its integration with id and cloud companies, its long-term safety advantages make it helpful.
What are the benefits of ZTNA over VPN?
ZTNA has many benefits over VPN, together with broader checks of each person and machine, extra granular entry granted, and ongoing checks. These measures make it tougher for unhealthy actors to achieve and keep entry to assets.